Bot Mitigation Definition
Approximately half of all traffic online comes from bots. It is critical to manage bot traffic, because both helpful and malicious bot traffic exists.
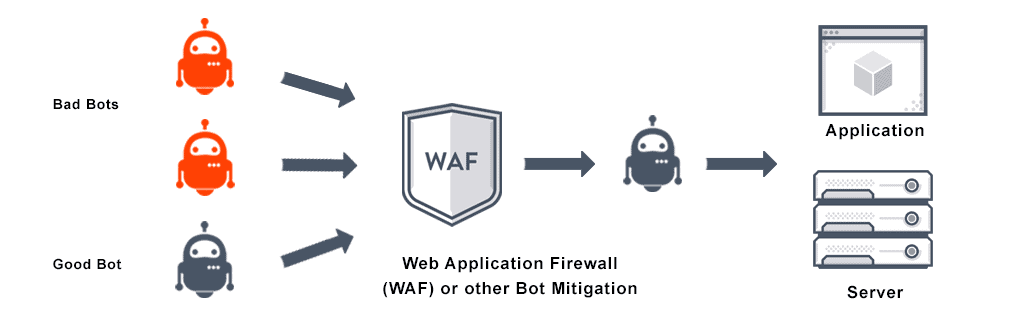
Bot mitigation involves identifying bot traffic and reducing or blocking bot threats in that traffic—any action or automated abuse of functionality that adversely impacts an application. Bots that are malicious launch Distributed Denial of Service (DDoS) attacks, hoard resources, steal intellectual property (IP), or perform credential stuffing and account takeovers.
Bot Mitigation FAQs
What is Bot Mitigation?
Bot mitigation includes identifying bot traffic, assessing its nature, and reducing risk. There are both helpful and harmful bots online. Many we rely upon for things like search functionality.
Malicious bots can pose any number of threats. They may launch DDoS attacks, engage in credential stuffing and resource hoarding, commit intellectual property theft, perform account takeovers, or cause other problems. Bot mitigation techniques identify and block bad bot traffic and any bot threats approaching your network or application to reduce risk.
In any computing environment, the majority of threats begin with botnets. These networks of bots help cyber attackers achieve scale. Evolving bot technology can enhance the threat posed by botnets.
Typically, the users manipulating malicious bots are motivated by financial gain. As a result, here are some common bot-targeted industries:
Airlines and sites that sell tickets for events are constant targets of resource hoarding bots and denial of inventory bots. The challenge is to ensure that actual human customers can buy tickets or get seats at events.
Gaming sites are frequently subject to credential stuffing and other account takeover attacks. A successful attack allows the attacker to access not only the player’s sensitive data such as credit card information, but also in-game assets.
Financial institutions are also frequent targets of bot-related attacks, both online and at the mobile-based app level. Newer, more sophisticated bot malware can leave many applications vulnerable, and any site is subject to credential stuffing and related attacks.
Bot mitigation tools work to reduce the risk from these kinds of attacks by identifying bots, assessing their activities, and blocking any potentially dangerous behaviors.
Of course, modern bots and botnets can target almost any business. Some of the types of bots and botnets are described below.
Types of Bots and Botnets
Mitigating bots means understanding what they are and how they work. A software application that runs automated tasks online is an internet bot. Compared to the internet activity we humans get into, bot tasks are typically performed much more rapidly and are much simpler.
Some bots are helpful: Google uses its Googlebot application to crawl and index the internet for search. Other bots, however, are malicious. For example, many bots can scan sites for software vulnerabilities automatically and execute simple attack patterns.
What Is a Botnet?
A botnet is a network or web of computers connected on the internet, which are each running at least one bot. These infected devices communicate with the attacker through a Command and Control (C&C) center. Attackers can use botnets to access devices and their connections, send spam, perform Distributed Denial-of-Service attacks, and steal data.
There are many varieties of malware that attackers use to infect devices and target them for use in a botnet. Some botnets are massive, with the largest encompassing millions of computers. The most successful botnets can perpetuate themselves, by spamming other devices through infected machines to grow the botnet, for example.
Botnet operators most frequently deploy botnets for Distributed Denial of Service (DDoS) attacks, spam bot activity, as high-profile social bots, or in other large-scale malicious activity.
Types of Bots
Here are some of the most common types of active bots on the internet, both malicious and helpful.
Spider Bots
Spider bots, also called web crawlers or web spiders, follow hyperlinks and browse the web to retrieve and index web content. To process site content, spiders download and use HTML and other resources, such as JavaScript, CSS, and images. This is why large sites with lots of pages or images sometimes try to help spiders crawl them with instructions in a robots.txt file.
Scraper Bots
Scraper bots or scrapers aim to take online data offline for later reuse by reading websites and saving their data. This can mean anything from scraping web content for particular data points, such as scraping an eCommerce site for product names and prices, to scraping entire web pages for content.
If web scraping sounds potentially problematic, that’s correct. Web scraping ranges from permitted or at least legitimate activity to web scraping that steals copyrighted intellectual property or sensitive data.
Download Bots
Users can deploy download bots to automatically download mobile apps or software, helping an app reach the top of the charts and influencing download statistics. Attackers also launch application-layer Denial of Service (DoS) attacks using these automated programs.
Spam Bots
A spambot or spam bot is an internet application that creates spam mailing lists by collecting email addresses from businesses and organizations, websites, and social media platforms. This may sound innocent enough, but cyber attackers can do much more than send spam email to a large list of email addresses.
Once on a spam list, an email recipient is subject to any number of phishing attacks. Spambot operators also favor form spam, automatic insertion of spam such as malware links or ads into forms for feedback or comments on popular websites. Credential cracking to gain unauthorized access to accounts is another typical problem arising from spambot attacks.
Indirectly, spam bots can also increase costs for Internet Service Providers (ISPs) and choke server bandwidth.
Social Media Bots
Many users operate bots on social media networks to advocate ideas, generate and respond to messages automatically, follow users, and gain fake followers themselves. At least one study estimates that 9 to 15 percent of Twitter accounts are actually social bots.
Ticketing Bots
Ticketing bots are applications that allow users to buy huge numbers of tickets to popular events in an automated way to resell them at a profit. This is often illegal, and almost universally an annoyance, as at least 40 percent of ticket sale traffic goes to bots.
Originally ticketing bot technology was easy to detect, but today it is much more sophisticated. Now ticketing bots parse JavaScript and accept cookies. The most advanced bots can even click on-page elements, making it much tougher to detect these bots.
What is Bot Management?
In recent times there has been some discussion of bot mitigation versus bot management among bot mitigation vendors. The idea is that bots are a fact of life online, and that merely blocking bots and then inspecting them all is an inefficient, short-term solution to a growing threat. The thinking is that the IT mindset should transition from the question of how to mitigate bots and bot mitigation to bot management, because blocking all bots even temporarily to assess their function is unsustainable.
However, there is no question that it is impossible to categorize most bots as solely helpful or malicious. Operator intent is a much more important factor than type of bot, for example. Industry and type of business are also critical factors.
The best bot traffic solutions offer both security and transparency. Bot behavior is best assessed in context. A bot mitigation solution that merely blocks all traffic does not offer a level of insight or control that is ideal, not least because even a blocked attacker can try again if the business does not understand the nature of the attack.
What is Bot Mitigation Software?
Bot mitigation software protects web applications and websites from malicious bot traffic and activity. This might include content scraping and IP theft, credential stuffing attacks, or resource hogging.
Software from bot mitigation vendors can use various means to identify and block these bots, either in bulk (e.g. IP denylisting) or task-by-task. There are some bot mitigation services and tools that work together in tandem, and others that are alternative products.
Bot mitigation solutions are part of a larger application security strategy. These tools are linked to DDoS protection tools, security solutions designed to prevent applications and websites from being overwhelmed by high-volume bot traffic.
Businesses use bot detection and mitigation software to defend against unauthorized bot activity, including attacks. Bots may attempt to scrape data from a website, hamper site performance, perform fraudulent transactions, or perform an all out DDoS attack. Products for bot detection and mitigation identify malicious bots, recognize bot activity, and stop harmful bots from engaging with applications, websites, or networks.
The difference between these solutions and DDoS protection software is that bot detection and mitigation tools defend against a range of malicious or risky bot-related activities, not just one kind of attack. Businesses use these bot mitigation solutions to stop bots from achieving their objectives and to maintain availability during attacks.
To serve as an effective bot detection and mitigation tool, a product should monitor all applications, websites, and networks for all bot-related activity. It should then determine which activities are malicious, and prevent access to all activities and other identified sources of danger.
Does VMware NSX Advanced Load Balancer Provide Bot Detection and Mitigation?
The VMware NSX Advanced Load Balancer delivers container ingress, software load balancers, and web application firewall services so applications are secure, available, and responsive. The VMware NSX Advanced Load Balancer provides scaling capacity, natively mitigating against dozens of DDoS attacks. The platform also offers customized protection, and visibility into attacks to prevent ongoing attacks. Bot mitigation using the platform’s WAF is a feature that is under development and coming soon.
For more on the actual implementation of load balancing, security applications and web application firewalls check out our Application Delivery How-To Videos.