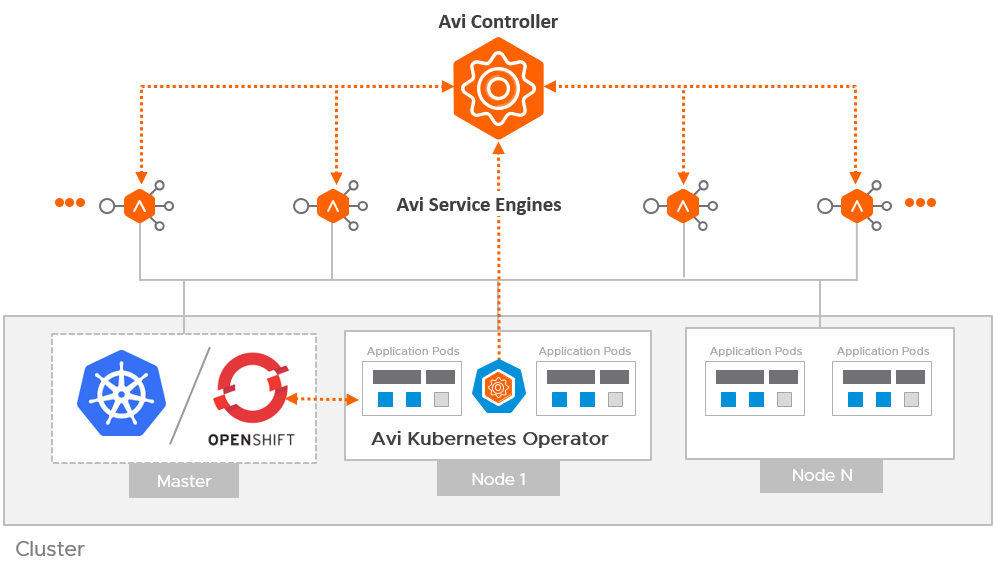
Avi Kubernetes Operator Version 1.5 Release Notes
The Avi Vantage platform integration with OpenShift/ Kubernetes provides a redesigned architecture involving a new operator called Avi Kubernetes Operator (AKO). The following illustration outlines the components of the Avi Kubernetes integration.
Issue Resolved in AKO 1.5.5
- Predefined health monitors are not assigned to a pool.
Key Change in AKO 1.5.5
- Hostrule is accepted if GSLB FQDN and local FQDN in the hostrule are the same.
Key Change in AKO 1.5.4
- In EVH deployment, if AKO is processing two hosts, that belongs to same parent virtual service, AKO continues to process the next host even if the current host has errors except if the error code is:
- Between 500 to 509
- 408, indicating session timeout
- 403, Controller upgrade is in progress
- 401, invalid credentials
What’s New in AKO Version 1.5.3
-
Support for multi-port Services with port number for ServiceType
NodePortandNodePortLocal -
Host rule rejection if GSLB FQDN and local FQDN in hostrule is same
-
Optimize bootup time on OpenShift setup by only working on the Secrets present on a namespace where AKO is installed
Issues Resolved in AKO Version 1.5.3
-
Added tenant and api version for fetching
authtoken -
AKO is not updating the pool members correctly in case of duplicate path present for the host.
What’s New in AKO Version 1.5.2
-
Boot up optimizations improves AKO’s boot time in scaled environments
-
Support for HTTPRule CRD for Routes without paths
-
Support for Service with multiple ports in EVH
Issues Resolved in AKO Version 1.5.2
-
Consider a Service object with multiple ports in Kubernetes. If this service is referred by an ingress host/path, prior to AKO 1.5.2 only a port name could be used. This constraint has been removed now and AKO accepts port numbers of a multi-port service as well in the Ingress definition.
-
In SNI deployment, Host rule CRD with
sslkeycertificatereference would get applied successfully to virtual service. However, upon deletion of this CRD, this virtual service would loose all cert configuration and get default cert. -
In EVH, certificates from all ingresses/ hostrule CRDs are placed into certificates of Parent virtual service. Prior to AKO version 1.5.2, certificate of one host was replaced by a certificate from another host when ingress with secret and host rule CRD with TLS configuration were applied to the same parent virtual service. With AKO version 1.5.2, certificate of each host is added/ removed individually from Parent virtual service.
Known Issues in AKO Version 1.5.2
-
Due to the use of Informers for Secrets, there is an adverse effect on boot up time in OpenShift based setups. AKO can further optimize the boot up time on OpenShift setup by filtering out the Secrets on
avi-systemnamespace. -
ServiceType of
NodePort/NodePortLocaldoes not support multi-port Services with port number.
What’s New in AKO Version 1.5.1
-
Support for programming FQDN for L4 services via Gateway object when
servicesAPIis set to true -
Support for Multi-Protocol (TCP/UDP) support in gateway virtual service (shared VIP)
Key Changes in AKO 1.5.1
-
Deprecated
subnetIPandsubnetPrefixin values.yaml, in favor ofcidrfield withinvipNetworkList -
Updated spec.network to include networkName and
cidrinformation inAviInfraSettingCRD -
The length of Avi object names is restricted to 255 characters in SNI deployment
-
Encoded Avi object names in EVH deployment
Known Issues in AKO 1.5.1
-
AKO update ingress status with VIP instead of public IP when public IP is enabled in public cloud deployments
-
AKO-created VIPs on AWS cloud may go down, if new FQDNs are added or removed from the Kubernetes Cluster ingresses. This issue has been fixed on the Controller version 20.1.6-2p5 for AWS.
Before upgrading to AKO 1.5.1 from any version of AKO, refer to the upgrade notes.
Document Revision History
| Date | Change Summary |
|---|---|
| October 08, 2021 | Published the Release Notes for AKO version 1.5.2 |
| August 31, 2021 | Published the Release Notes for AKO version 1.5.1 |